Marketing’s job is to drive buying processes at scale.
MEDIA 7: In your professional marketing career, how have you mastered the ability to combine the Arts and the Sciences to create meaningful customer experiences?
DIANE WALKER: The Creative:
Identifying a brand – most people can easily recognize familiar logos, signature colors, and entertaining campaigns, and that’s certainly part of it. But the real magic begins when you couple those thought-provoking and entertaining images with a clear, concise copy. Communicating with customers, prospects, and partners is a fine art. We focus on crafting messages using a casual narrative in a conversational tone. After all, B2B buyers are consumers too. The creative is the visual clue, designed to align with the story. We strive to engage the reader with a short story, providing insight into a business challenge they’re experiencing and how to solve for it. It’s no easy task to surprise and delight the audience while retaining the technology’s sophistication with informative and educational content. The key is to engage the reader by capturing their attention and creating intrigue to further illustrate customer benefits with desired business outcomes.
The Science:
We measure everything from overall marketing and sales performances to the tiniest detail. We monitor conversions from leads to revenue. Keeping a pulse on pipeline velocity has been a game-changer. Activities such as regular A/B testing, creating asset heat maps, and evaluating engagement trends are just a few ways we monitor the health of our programs. We are constantly evolving – process improvement, program experimentation and integration across all marketing channels are critical. We evaluate and adjust strategies and tactics as needed by restructuring low performers and replicating the components of our highest-performing content and programs. We leverage marketing automation, intent data, artificial intelligence, and machine learning to define audience profiles. The approach includes Account-Based Marketing, industry verticals, role-based targeting, re-engagement, and more. We are close partners with Marketing Operations. Our focus is to reach the right person at the right time with the right message. Creating an orchestrated, digital experience requires data-driven decisions, experimentation, and innovation.
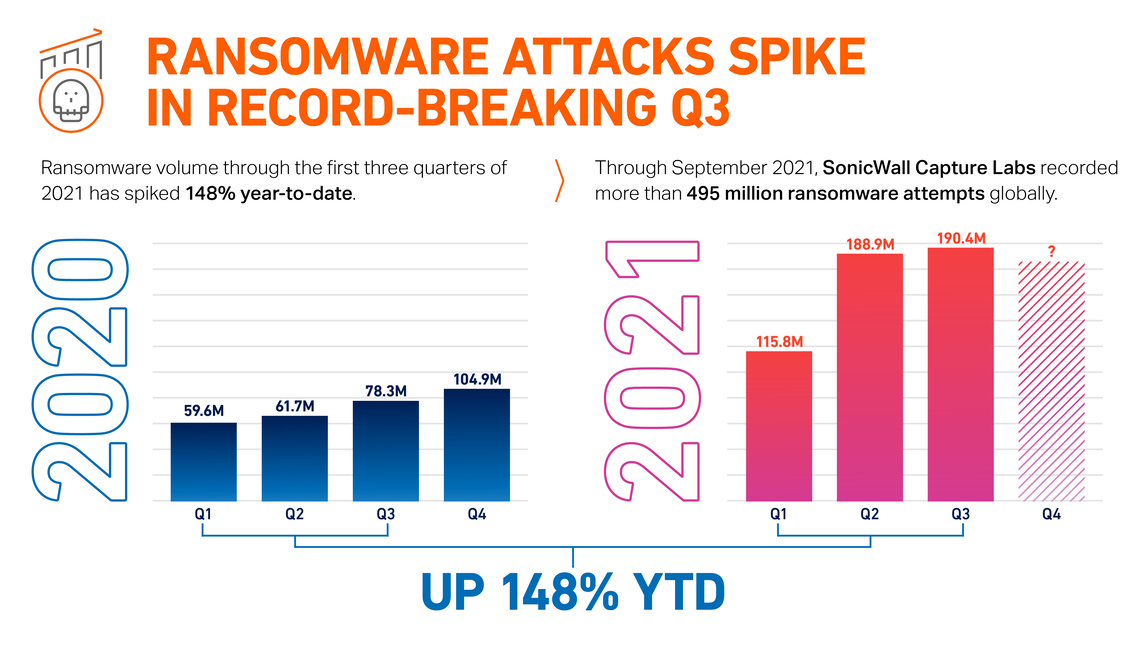
M7: How does SonicWall mitigate the risks for enterprises with remote and mobile workforces?
DW: To be effective, cybersecurity must provide mobile employees with easy and secure 24/7 access to key business resources in an agile, easy-to-use, cost-effective, and scalable way. This requires a zero-trust posture regarding any mobile device attempting to connect with corporate resources, whether those resources be on-prem or in the cloud. Secure mobile access is a core component of a zero-trust approach to anywhere, anytime access. IT must also secure access from these mobile endpoints with limited budgets and skilled staff resources. This means streamlining deployment, availability, and support to the lower total cost of ownership.
SonicWall
Secure Mobile Access provides distributed enterprises with comprehensive end-to-end secure remote access to corporate resources hosted across on-prem, cloud, and hybrid datacenters. It applies identity-based, policy-enforced access controls, context-aware device authentication, and application-level VPN to grant access to data, resources, and applications after establishing user and device identity and trust. SonicWall Central Management Server enables organizations, distributed enterprises, and service providers to centrally manage and rapidly deploy secure access solutions, either deployed on a private cloud as a virtual appliance or on a public cloud (AWS or Microsoft Azure) using Bring Your Own License (BYOL).
Read More: People now just want news that's true, says Ivar Krustok, Head of Data Science and IT at Ekspress Meedia
Communicating with customers, prospects, and partners is a fine art.
M7: SonicWall recently turned 30 as a global cybersecurity leader. As a team, how did you commemorate this milestone and what do you hope to achieve as you step into a new year?
DW: Throughout August 2021, SonicWall celebrated its heritage – the customers, employees, product innovation, and channel DNA that have helped shape SonicWall over the past three decades and will continue to inspire us in the years ahead. As a company, SonicWall celebrated its leadership and heritage across 30 years in the cybersecurity industry. We celebrated our customers for their loyalty and being part of decades worth of innovation and security. SonicWall recognized employees, the hard-working people who made the company what it is today — many of whom are still employed with us today. We highlighted our product innovation across three decades of growth.
SonicWall applauded its global partners who serve as the heartbeat of the organization, which has always been 100% driven by the channel. We armed our employees, customer communities, and partners with 30-year badges, banners, email signature blocks, and virtual meeting backdrops. There were contests with prizes for best photos and shared lots of memorable stories through blogs and social media posts. While the last five years were important chapters in this journey, we have more goals to achieve, milestones to mark, and history to be made. SonicWall is always forward-looking. And that’s how the company — and its people — has been a mainstay in the industry for more than 30 years.
M7: This year, SonicWall released three new high-performance firewall models. How can enterprises and large organizations around the world benefit from these new products?
DW: If we’ve learned anything during the unprecedented surge of malware and ransomware this year with 70% of full-time workers working from home in hybrid multi-cloud environments – we’re more vulnerable than ever. For organizations, it’s all about choice. SonicWall’s growing virtual, cloud, and hybrid offerings leverage the best of the company’s Boundless Cybersecurity approach to provide deployment choices to the customer while solving real-world use cases faced by SMBs, enterprises, governments, and MSSPs. This year, we launched the power and flexibility of the 7th generation firewall advancements that bring enterprises to a level where they can stop attacks from many vectors.
Our vision for cybersecurity is to protect organizations from the broadest spectrum of intrusions, pre-emptively reduce cyber risk, and achieve greater protection across devices, new perimeters, and network segments more efficiently while lowering the total cost of ownership. Our next-generation firewalls protect organizations from the broadest spectrum of intrusions, pre-emptively reduce cyber risks, and achieve greater protection across devices, new perimeters, and network segments more efficiently while lowering the total cost of ownership.
Read More: Listen to your customers, advises Christopher Penn, Co-Founder and Chief Data Scientist at TrustInsights.ai
Creating an orchestrated, digital experience requires data-driven decisions, experimentation, and innovation.
M7: What does modern-day marketing mean to you and how do you leverage these developments to facilitate increased demand and business growth?
DW: Marketing’s job is to drive buying processes at scale. Communicating with both customers and prospective customers where they are engaged is key. If our audience understands the message, then that message will create a brand affiliation to help them move forward in the buying process. The buyer’s journey is not linear. Decisions are made by diverse buying groups with different needs and engagement patterns. We need to reflect on the multi-stage, multi-touch digital buyer journey.
Marketing platforms, tools, and processes have come a long way over the past decade. It’s exciting to see the advancements in data intelligence. Data is the answer to a more effective digital transformation. It shows us where to find opportunities and gives us insight into how we can win more business. Connecting with Sales makes a measurable impact. We are enabling front-line qualification sales teams with lead information that includes the context of what product or solution the account has shown interest in, suggested contacts to follow up with, and content to start those outreach conversations.
M7: According to you, what are some of the best practices for effective marketing strategies that drive business growth?
DW: There are so many components to an effective marketing strategy. “Know thy customer” is the golden rule. Profiling the ideal customer helps us formulate strategies to pursue net new customers. Who are they? What do they care about? When are they typically ready to buy? Where are we successful in helping them solve their business challenges? How do we create real business value? Why choose SonicWall? Understanding the customer experience is paramount to customer satisfaction as well as net-new customer acquisition. Based on your Ideal Customer Profile (ICP), you can build the propensity to buy models which will lead to net-new opportunities.
Today’s marketers must be revenue marketers. Guideposts include: Understanding the business, monitoring and interpreting performance metrics, and creating targeted pipeline acceleration programs to increase revenue velocity to closed-won revenue.
This year, the demand generation team has been focused on innovation and integration. Innovation for us means embracing new ideas and trying new approaches and tactics – everything from creative services and messaging to marketing operations and sales. We have had tremendous success leveraging automated nurture programs within our Marketing Automation Platform (MAP). Integration planning across the marketing and sales ecosystem is being achieved through collaboration between the marketing and field organizations. To date, our efforts have paid dividends. One company, one voice.